Tailored Corporate Protection Solutions for Your Special Service Needs
In today's significantly complicated organization landscape, making certain the protection and defense of your organization is of extremely important importance., we recognize that every business has its very own unique collection of safety requirements. That is why we use customized company safety and security services created to deal with the certain obstacles and susceptabilities of your company.
Examining Your Particular Safety Requirements
To effectively address your organization's protection problems, it is vital to carry out a detailed analysis of your details protection requirements. Understanding the unique dangers and vulnerabilities that your business encounters is crucial for creating a reliable safety technique. Without a proper analysis, you might allocate resources inefficiently or ignore important areas of susceptability.
The initial action in assessing your particular security needs is to perform a thorough examination of your physical properties, consisting of structures, car parking locations, and access factors. In addition, it is essential to evaluate your company's electronic safety by reviewing your network infrastructure, data storage space, and security protocols.
One more important element of analyzing your protection requires is recognizing your company's special functional demands and compliance responsibilities. This consists of considering factors such as the nature of your industry, the value of your possessions, and any legal or regulative demands that may apply. By understanding these certain variables, you can customize your protection gauges to satisfy the certain demands of your service.
Personalizing Surveillance Systems for Ideal Security
Personalize your monitoring systems to offer optimal security for your service. When it involves securing your company and its properties, a one-size-fits-all method simply will not be sufficient. Every organization has its very own one-of-a-kind safety needs, and tailoring your surveillance systems is vital to making certain that you have the most reliable security in area.
First and foremost, it is vital to conduct a thorough assessment of your properties to recognize susceptible locations and prospective safety risks. This will aid determine the type and variety of video cameras needed, as well as their critical placement. High-risk locations such as entrances, car park, and storage space centers might require advanced surveillance modern technology, such as high-resolution cameras or night vision abilities.

Incorporating your security systems with other safety and security steps, such as gain access to control systems or alarm, can even more improve the performance of your total protection approach. By tailoring your security systems to align with your particular company demands, you can have comfort recognizing that your consumers, properties, and staff members are shielded to the maximum degree possible.
Applying Tailored Access Control Actions
For ideal safety, companies need to implement customized accessibility control actions that straighten with their one-of-a-kind service requirements. Access control measures are crucial in securing sensitive information and making certain that just authorized people have access to specific areas or sources within a business. By customizing accessibility control procedures, companies can develop a durable safety and security system that efficiently mitigates safeguards and threats their possessions.
Executing customized access this post control steps involves numerous vital steps. A thorough analysis of the company's safety demands and possible susceptabilities is essential (corporate security).
Gain access to control actions can consist of a mix of physical controls, such as keycards or badges, as well as technological options like biometric authentication or multi-factor authentication. These steps can be carried out throughout various entry points, such as doors, gates, or computer system systems, depending upon the company's particular demands.
In addition, companies must establish clear policies and treatments regarding accessibility control. This includes defining functions and responsibilities, establishing individual access degrees, frequently evaluating gain access to benefits, and keeping an eye on gain access to logs for any dubious activities. Normal training and recognition programs must likewise be conducted to ensure employees understand the relevance of gain access to control and abide by established protocols.
Enhancing Cybersecurity to Safeguard Sensitive Information
Executing durable cybersecurity procedures is crucial to properly secure delicate data within a firm. In today's digital landscape, where cyber threats are becoming increasingly innovative, organizations need to prioritize the defense of their valuable info. Cybersecurity includes a series of methods and innovations that intend to prevent unauthorized gain access to, information breaches, and various other malicious activities.
To improve cybersecurity and guard sensitive information, companies should apply a multi-layered technique. This consists of utilizing innovative security methods to shield data both in transportation and at remainder. Security guarantees click over here that also if information is intercepted, it stays unusable and unreadable to unapproved people. Additionally, carrying out strong gain access to controls, such as multi-factor authentication, can assist protect against unauthorized access to delicate systems and details.
Furthermore, companies must have a case feedback strategy in position to successfully respond to and minimize any kind of cybersecurity occurrences. This plan should detail the steps to be taken in the occasion of an information breach or cyber attack, consisting of interaction protocols, control procedures, and recovery approaches.
Ongoing Support and Upkeep for Your Unique Needs
To make sure the ongoing effectiveness of cybersecurity actions, continuous assistance and maintenance are important for addressing the progressing threats encountered by services in protecting their sensitive information. In today's rapidly transforming digital landscape, cybercriminals are regularly locating new ways to exploit susceptabilities and violation safety and security systems. Therefore, it is vital for organizations to have a robust assistance and upkeep system in position to remain in advance of these threats and secure their useful information - corporate security.
Ongoing assistance and upkeep involve consistently updating and covering safety software program, keeping an eye on network activities, and performing vulnerability assessments to identify any weaknesses in the system. It likewise includes giving timely support and support to staff members in executing safety ideal techniques and reacting to possible protection occurrences.
By investing in ongoing assistance and upkeep services, services can benefit from positive monitoring and detection of potential hazards, along with punctual action and removal in case of a safety and security breach. This not only helps in reducing the impact of a strike yet additionally makes certain that the company's protection pose continues to be versatile and strong to the developing threat landscape.
Verdict
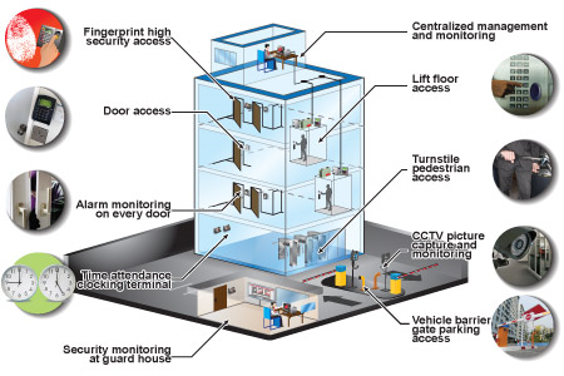
To properly address your organization's safety problems, it is important to carry out a thorough assessment of your particular safety and security requirements. Every organization has its own unique safety needs, and personalizing your security systems is key to making certain that you have the most reliable defense in area.
For optimal safety and security, business need to carry out customized gain access to control procedures that align with their special service requirements.In final thought, tailored corporate safety and security options are essential for businesses to address their one-of-a-kind protection demands. By evaluating specific safety requirements, personalizing surveillance systems, executing customized access control procedures, and enhancing cybersecurity, organizations can safeguard sensitive data and shield versus prospective risks.